What is Secure Boot? The Foundation of IoT Security.
Learn why Secure Boot, a process for authenticating IoT device firmware, is critical for building safer connected products.
Ready to build your IoT product?
Create your Particle account and get access to:
- Discounted IoT devices
- Device management console
- Developer guides and resources
What Is Secure Boot?
In the context of Internet of Things security, Secure Boot refers to the process of authenticating a device’s firmware and operating system against a known secure cryptographic key placed on the device at the time of manufacture. This authentication occurs every time the device is booted to validate that the firmware or code being loaded is the legitimate version that was placed there by whoever produced it.
With Secure Boot, a bad actor who gains physical access to a device embedded in an IoT system or product would be unable to boot the device with their own modified firmware or bootloader, as this wouldn’t cryptographically match the secure key implemented by the manufacturer.
Why Is Secure Boot So Important for IoT Device Security?
Secure Boot is one of the most important security features in any IoT product. When physical products are connected to the Internet, they become vulnerable to cyberthreats—as such, manufacturers must not only consider physical security, but also cybersecurity practices pertaining to the device firmware, connectivity, and application ecosystems that surround their products.
One of the most common attack vectors for physical devices involves a bad actor getting physical access to an IoT device or gaining remote access via a port scan. Once they do this, they can assume control by booting the device with their own firmware. This can lead to undesirable device behavior, stolen business or customer data, or loss of the device.
Secure Boot makes this difficult—if not impossible—because the device is signed with a cryptographic key when it’s manufactured. If the firmware doesn’t match the key, the device simply won’t work, thereby thwarting the bad actor.
Check out our IoT security checklist for more common threats to IoT products.
How Does Secure Boot Work?
Secure Boot can be thought of as a series of validation layers that mutually check each other when a device powers on and loads its embedded software. A lot of physical device attacks take the form of manipulating the boot process into causing the device to behave in an incorrect manner, perhaps by loading manipulated software.
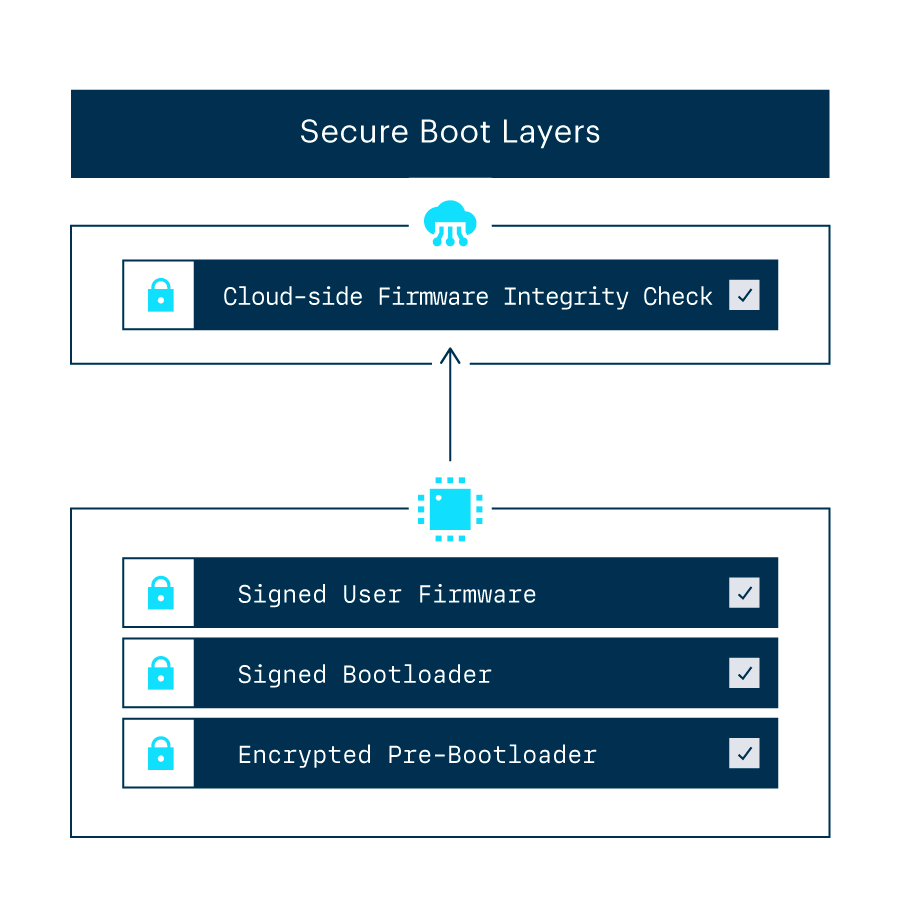
By using cryptography to protect the initial bootup instructions via strong encryption and then authenticate the next layer of instructions via digital signatures, a device will not allow itself to boot up modified or unsigned software. The P2 is the first Particle product to ship with the initial version of secure boot enabled, with more features to support additional layers on the way.
At Particle, we’ve always performed a cloud-side firmware integrity check—meaning that when a device comes online and connects to our device cloud, we validate that the installed firmware matches what is expected of the code.
The Secure Boot process allows for a bottom-up check in addition to Particle's top-down approach, allowing the device to perform cryptographic validation offline before a cloud connection is established. This dual approach makes for a highly secure platform suitable for a variety of hardware applications.
Examples of Secure Boot in Action
So, which industries are designing products with Secure Boot functionality?
Electric Vehicle Charging Manufacturers
Many countries are moving forward with the electrification of the transportation industry. In particular, the U.K.—which has assumed a leading role in the movement—is taking great strides to ensure that EV infrastructure is not only widely available but connected.
The Electric Vehicles (Smart Charge Points) Regulations 2021 legislation that took effect in the U.K. on June 30, 2022, requires all public and private EV chargers to be Internet-connected. These regulations include strict security requirements for connected EV chargers, including Secure Boot. More specifically, all EV chargers will have to support an enhanced security scheme that includes Secure Boot by January 1, 2023.
Here’s a snippet of the regulatory requirements:
*(3) A relevant charge point must be configured so that— (a) it checks, when it is first set up by the owner, and periodically thereafter, whether there are security updates available for it; (b) it verifies the authenticity and integrity of each prospective software update by reference to both the data’s origin and its contents and only applies the update if the authenticity and integrity of the software have been validated;
(4) A relevant charge point must be configured so that— (a) it verifies, via secure boot mechanisms, that its software has not been altered other than in accordance with a software update which has been validated in accordance with sub-paragraph (3)(b) above; (b) if an unauthorised change to the software is detected, it notifies the owner and does not connect to a communications network other than for the purposes of this notification.*
In the context of individual EV chargers or charger networks, Secure Boot is a vital security practice that prevents negative outcomes such as:
- Energy theft
- Impeded charging
- Stolen customer or business data
- Access to system owners’ home Wi-Fi networks
- Physical equipment and infrastructural damage due to malicious or improper usage
Industrial Control and Automation Systems
As demonstrated by ongoing conflicts, the battlefield has evolved to include highly specialized operations against critical infrastructure and industrial control systems. Standards like the IEC62443 have been designed to reduce the risk of malicious actions to these types of devices.
It doesn’t take much imagination to understand how damaging a targeted attack to critical infrastructure can be, which is why devices that have a direct impact on power, water, gas, and other utilities need to be specifically hardened against both remote and physical attacks.
Implementing Secure Boot in Your Own IoT Products
In this section, we’ll dive into the major steps you need to take to build Secure Boot into your IoT products.
Start With Secure Boot-Enabled Devices
Many open source devices and platforms like Raspberry Pi and Arduino run a version of embedded Linux that leading penetration testing company Pen Test Partners said could lead to “easy extraction of all stored data, including credentials and the Wi-Fi Pre-Shared Key.”
These modules are popular for prototyping, with some companies even using them in their production processes—but while they’re inexpensive and easy to use, they often fall short of reasonable enterprise-grade security standards.
Most open source device firmware doesn’t come with Secure Boot functionality off the shelf, and it’s hard to tell if the proper security steps have been taken when devices are sourced from third-party manufacturers. This leaves devices open to bad actors who can get root access to the device firmware, run their own firmware on it, and assume device control as a result.
That’s why hardware security must be your first concern when evaluating devices.
Because Particle owns its manufacturing and production capacities, every Particle device is signed with an individual key at the time of manufacture that ensures compliance with most Secure Boot requirements.
Our Secure Boot mechanism is backed by Fortanix HSM, which is used in highly secure communications devices for enterprise and government use. Our newest IoT Wi-Fi modules, the Photon 2 and P2, are manufactured with built-in encrypted flash and ARM TrustZone technology.
- Encrypted flash prevents malicious actors from taking chips off the board and reading their contents, as everything is garbled without the key set at the factory.
- ARM TrustZone is a well-known mechanism that provides a layer—or “zone”—of trust between the secure device functions and the operating system. With it, the parts of the device that generate cryptographically secure keys and the general user space where you write your firmware are separated by a layer of abstraction, ensuring the areas that require absolute integrity cannot be manipulated.
Check out our in-depth comparison of Particle vs. Arduino to see how Particle provides an extra layer of security out of the box.
Use a Hardened and Stable Device Operating System
Open source OSs often expose code irrelevant to a device’s function, which makes the device vulnerable to potential threats like port scans. If you don’t have a team that knows how to reduce the attack surface of the device firmware, you may unwittingly expose yourself—and your customers—to cyberthreats.
By contrast, Particle devices come pre-integrated with our embedded IoT operating system, Particle Device OS, which includes:
- Minimal attack surface. Particle Device OS has no open ports and leverages only services that are essential to connect to the Particle Cloud. By removing the extra fluff included in most open source OSs, Particle Device OS is secure and ready to use right out of the box.
- Abstracted APIs. Particle Device OS abstracts the complex integration among microcontrollers, modems, peripherals, verified libraries, and your application firmware, setting up your product’s physical device to work seamlessly and securely.
- Long-term support versions. Particle Device OS LTSs are independent branches of the operating system that are feature-frozen in time—in other words, they do not receive updates with new features, API changes, or improvements that change device function or standard behavior. These versions are covered by an extended support window to address bugs, regressions, and vulnerabilities.
- Over-the-air updates. Particle OTA Services lets you push OTA updates with a single line of code or a few clicks, making it simple to add new features, respond to security vulnerabilities, and change product behavior after you’ve shipped. Learn more about IoT OTA updates.
Build a Secure and Encrypted Data Pipeline
Security doesn’t just happen directly on the device; the cloud side must also provide an extra layer of security through integrity checks to verify that the correct version of the firmware is running when the device boots. If an unexpected input or code change appears, your cloud solution should prevent booting and alert you.
Particle Cloud, our secure and reliable IoT device cloud, does this for you as soon as you turn on any Particle device.
Here’s what Particle Cloud provides from a security standpoint:
- The modules are bound to your account only, with limited access and two-factor authentication employed for secure access to the cloud management interface. Your devices cannot be moved to another account for OTA reprogramming, and only you can unclaim a device from your account.
- Devices are paired with the cloud platform and reverse-connect to a trusted endpoint used for further connectivity.
- Devices are authenticated as they connect to the cloud using public key cryptography. This process assures that the cloud is what it purports to be and is not rogue.
- Particle Cloud knows what firmware to expect. If that firmware doesn’t show up when the device connects, the cloud will intervene in real time to fix the issue with an update, thereby protecting against firmware modification attacks.
- Particle Cloud doesn’t store event payloads or any proprietary information belonging to you or your customers. Rather, storage is limited to diagnostic data that is used solely to ensure optimal device performance and gets auto-purged regularly.
Secure Boot is a foundational practice for securing IoT devices and products. Don’t let your devices live out in the field with critical vulnerabilities—equip your products with Secure Boot-enabled devices and an integrated IoT Platform-as-a-Service to easily ship products without compromising security.